

Having someone steal a password from your organization is easier than you might think.
With any of these common actions, any user could run the risk of being stolen the password:
If someone steals a password and accesses your system, he can get sensitive data, erase information and cause damage that can impact your business and your reputation.
Are you completely sure than a password from your organization will never be stolen?
2-Step Authentication will protect your system from malicious users even if they have stolen a password.
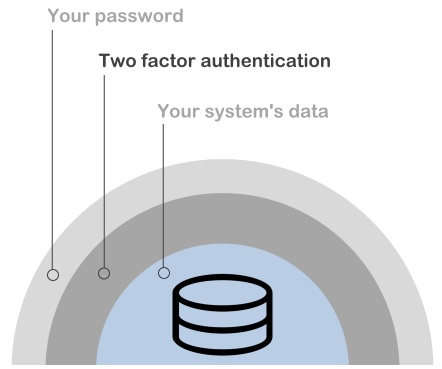
Most systems only have one security layer, the password, to secure the access.
With two factor authentication if a hacker breaks the security layer of the password, he still needs the authenticated user's smartphone to access to your system.
If the user's phone is stolen, the device can be deactivated on the platform so it will not be useful to access the system.
With two factor authentication you will protect your system with something user knows (his password) and something he owns (his smartphone with a validated app).
If the user's phone is stolen, the device can be deactivated on the platform so it will not be useful to access the system.

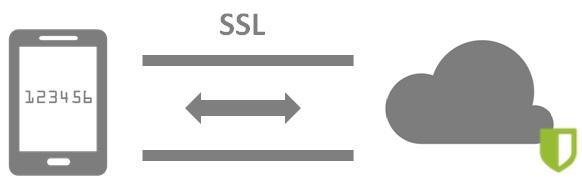
Codes are created on demand and are sent to user's phone through a secured SSL connection to avoid sniffers and 'man in the middle' attacks.
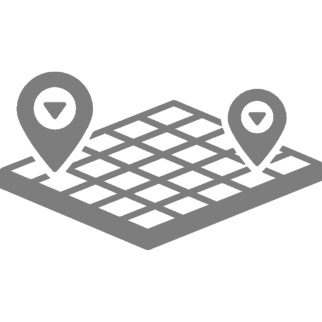
If geolocation validation is enabled, even if the users use the app from their verified devices, they will not be able to access the site if they are outside the allowed zones.
This way you can prevent users from accessing the site outside the work area in cases where the access policy establishes it.
Amateurs hack systems, professionals hack people.
In a brute force attack an individual or a large botnet of infected machines generate millions of combinations to access the accounts. Brute force is the oldest attack vector.
All login forms can be attacked with brute force.
Signum Pass protects against brute force, as the attack never exceeds 2-step authentication.
In a man in the middle attack, an attacker intercepts communications between the users and the site where they’re logging in.
Attackers steal secrets in transit.
Signum Pass is not vulnerable to this attack, as communication with the device is safe and each validation is generated in real time.
In a keylogging attack, the attacker installs malware on a device that records the user's typing to steal passwords or sensitive information.
Keyloggers steal passwords.
Signum Pass generates single-use codes and has functionality in which the user does not have to type any code.
In a phishing attack, a criminal tries to collect sensitive information such as user names, passwords and bank data, posing as a real entity in an electronic communication.
Phishing takes advantage of weaknesses and carelessness inherent in human nature.
Signum Pass does not use passwords, so this point of attack is obliterated.
All the information that Signum Pass sends and receives from the user goes through a secure SSL connection, compared to the SMS that are sent in plain text and that can be intercepted by anyone near the user.
Signum Pass is not another attractive feature, it is a key piece in the Access security policy.
Sending SMS on a continuous way is expensive. If you want to protect the access of all users via SMS, it would be prohibitively expensive to send an SMS for every login happening on a site.
With Signum pass the price is not based on the number of logins, but in the number of users of the system. Signum Pass does not rely on the telephone infrastructure, so it offers an unlimited number of logins at no additional cost.